An information security program is a critical component of any organization regardless of the size of your business or the industry you’re in.
A good information security program consists of a comprehensive set of information security policies and procedures, which is the cornerstone to any information security program. Whether you’re responsible for protected health information (PHI), personally identifiable information (PII), or any other proprietary information, having a fully developed information security program provides you with a holistic approach for how to safeguard and protect the information for which you are responsible.
What is an Information Security Program?
Building an information security program means designing and implementing security practices to protect critical business processes and IT assets. These security practices that make up this program are meant to mature over time. An information security program also helps to define policies and procedures for assessing risk, monitoring threats, and mitigating attacks.
A good information security program clearly defines how your organization will keep your company’s data secure, how you will assess risk, and how your company will address these risks. Designating an information security officer can be helpful in this endeavor to help organize and execute your information security program. A great place to start when developing any information security program is to identify the people, processes, and technologies that interact with, or could other have an impact of the security, confidentiality, or integrity of your critical assets.
Importance of an Information Security Program
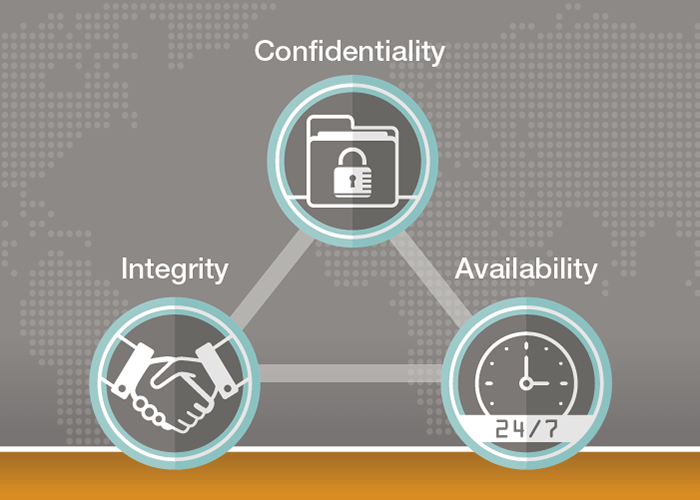
As previously mentioned, an information security program helps organizations develop a holistic approach to securing their infrastructure, especially if regulations mandate how you must protect sensitive data. In information security, there are what are known as the “pillars of information security”: Confidentiality, Integrity, and Availability (CIA). Consequences of the failure to protect those pillars could lead to the loss of business, regulatory fines, and loss of reputation. Applying appropriate administrative, technical, and physical safeguards through an information security program can help you to protect the confidentiality, integrity, and availability of your organization’s critical assets.
Let’s take a look at how to protect the confidentiality, integrity, and availability of proprietary data.
Confidentiality
Maintaining confidentiality is important to ensure that sensitive information doesn’t end up in the hands of the wrong people. In order to do this, access must be restricted to only authorized individuals. Some methods that could be used to protect confidentiality include encryption, two-factor authentication, unique user IDs, strong passwords, etc.
Integrity
Maintaining the integrity of sensitive data means maintaining its accuracy and authenticity of the data. This means that sensitive data must be protected from accidental or intentional changes that could taint the data. File permissions and access controls are just a couple of things that can be implemented to help protect integrity.
Availability
Maintaining availability means that your services, information, or other critical assets are available to your customers when needed. This doesn’t just apply to lost or destroyed data, but also when access is delayed. Developing a disaster recovery plan and performing regular backups are some ways to help maintain availability of critical assets.
Sarah Morris is a guest blogger from auditor KirkpatrickPrice. The original blog post may be found here. For additional information on security program best practices, visit the Center for Internet Security (CIS) or contact Sarah at [email protected].

