On the Blog
Check out AISN’s collection of news, expert advice and tips on cloud, security, regulatory compliance and more.
- All
- Active Directory
- Applications
- Blog
- Cloud Enablement
- Cloud Solutions
- Compliance
- Design & Development
- Education
- Federal
- Financial Services
- Government
- Health Care
- Healthcare
- HIPAA
- IAM
- Information Security
- Infrastructure
- Managed Services
- Manufacturing
- Security & Privacy
Why More Universities Are Choosing Azure for Educational Institutions
July 26, 2016
Cloud Solutions
Is it time to join the other 750+ universities using Microsoft Azure? Microsoft Azure offers a powerful, flexible cloud platform with a global network of ...
Read More →
Call Monitoring Compliance
June 1, 2015
Compliance
It’s important to analyze and fully understand the areas of risk as the CFPB continues to closely supervise the collections environment and call monitoring compliance. ...
Read More →
Understanding PCI DSS Requirements 1 and 2: A Guide for Shared Hosting Providers
May 13, 2015
Compliance
If you’re a shared hosting provider or a business using shared hosting, understanding the Payment Card Industry Data Security Standard (PCI DSS) requirements for shared ...
Read More →
PCI DSS Gap Analysis: A Complete Guide to Identifying and Closing Compliance Gaps
February 25, 2015
Applications
Meeting PCI DSS requirements starts with understanding where your organization stands today. That’s where a PCI DSS gap analysis comes in. It’s a diagnostic process ...
Read More →
Microsoft BizSpark FAQs
February 11, 2015
Applications
AIS Network has participated in the Microsoft BizSpark program since it began about 5 years ago. We love our BizSpark friends, the program and everything ...
Read More →
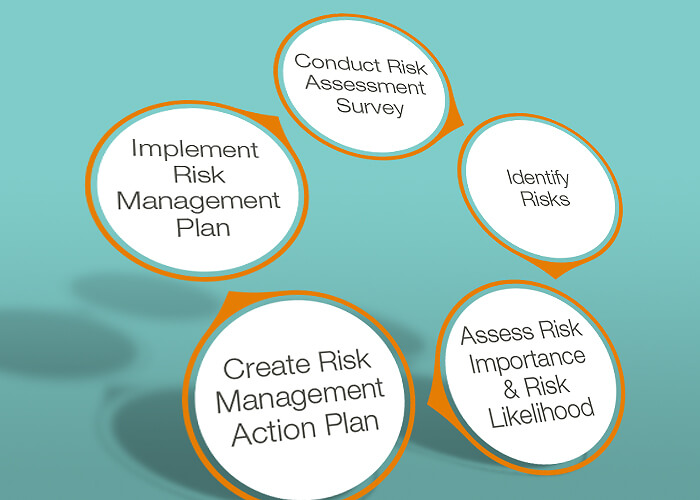
Mastering a Risk Assessment
February 5, 2015
Compliance
In light of the recent news of the data breach at Anthem Blue Cross/Blue Shield, risk assessment is our theme today. We welcome this guest ...
Read More →
HIPAA Audit Programs: What Covered Entities and Business Associates Need to Know
January 2, 2015
Compliance
The U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) is continuing its efforts to enforce HIPAA compliance through periodic and ...
Read More →
Public Cloud vs VPS
March 4, 2014
Cloud Solutions
When it comes to virtualized environments, we’re often asked: What’s the difference between a Virtual Private Server (VPS) and a public cloud? Both leverage virtualization, ...
Read More →
Cleaning Out the SharePoint Site Recycle Bin
July 16, 2012
Applications
By Terry EngelstadMCP, MCSE, CCNA, MCDBA, MCTS, MCITPAIS Network Operations Manager Recently, a SharePoint hosting customer asked us to perform routine maintenance on his SharePoint site. ...
Read More →
Why Hosting SharePoint in the Cloud Makes the Most Sense for Large Enterprises
March 21, 2012
Blog
When it comes to hosting SharePoint in the cloud, large enterprises face a big decision: choose public, hybrid, or private cloud deployment. While public and ...
Read More →
What Is Microsoft Office 365? What Is SharePoint Online? (Part 1 of 2)
January 11, 2012
Applications
What is Microsoft Office 365? In June 2011, Microsoft released Office 365, essentially bundled online software hosted in the cloud. Office 365 replaced Microsoft’s Business ...
Read More →
A Partner You Can Trust
At AISN, we don’t believe that “one size fits all” is the way to offer cloud solutions. Our business model is built on the belief that our clients deserve customized cloud platforms designed to meet their specific compliance, security and operational needs.
If you have questions about the cloud or cloud enablement services, we have answers. Our experts are always happy to discuss your needs, so get in touch with us today.