On the Blog
Check out AISN’s collection of news, expert advice and tips on cloud, security, regulatory compliance and more.
- All
- Applications
- Blog
- Cloud Enablement
- Cloud Solutions
- Compliance
- Design & Development
- Education
- Federal
- Financial Services
- Government
- Health Care
- Healthcare
- HIPAA
- Information Security
- Infrastructure
- Managed Services
- Manufacturing
- Security & Privacy
What to Expect From a Penetration Test Report
August 10, 2018
Security & Privacy
What to Expect From a Penetration Test Report Let’s face it. There are a lot of bad actors out there, and they are working to ...
Read More →
Risk Assessments Can Save Your Business
February 19, 2018
Government
Risk Assessments Can Save Your Business Think risk assessments can save your business? You’re right. A risk assessment is a critical component of any organization’s ...
Read More →
Employee Cyber Security Training
January 15, 2018
Managed Services
Employee Cyber Security Training Do your employees lack cyber security training? Human error is one of the greatest threats to organizational security – after all, ...
Read More →
Ensuring Security and Compliance
December 28, 2017
Compliance
Most organizations tend to focus on becoming compliant rather than being secure. And while meeting client requirements and industry regulations is very important, it does ...
Read More →
Information Security Program Is Critical
November 27, 2017
Education
An information security program is a critical component of any organization regardless of the size of your business or the industry you’re in. A good ...
Read More →
KRACK Security Flaw Protection
November 10, 2017
Education
Researchers have discovered a new weakness found in the WPA2 protocol (Wi-Fi Protected Access 2), the security method which protects all modern Wi-Fi networks, known ...
Read More →
Steps to Avoid a Pricey Data Breach
October 17, 2017
Blog
Are you swimming in information security concerns? Avoid a pricey data breach by reading further. Recent and startling new malicious attacks are causing organizations to ...
Read More →
What’s Driving Your Cloud Initiatives?
August 19, 2017
Infrastructure
What business goals or objectives are driving cloud initiatives at your company? Could they be among these? Lower total cost of ownership (TCO) Improving customer ...
Read More →
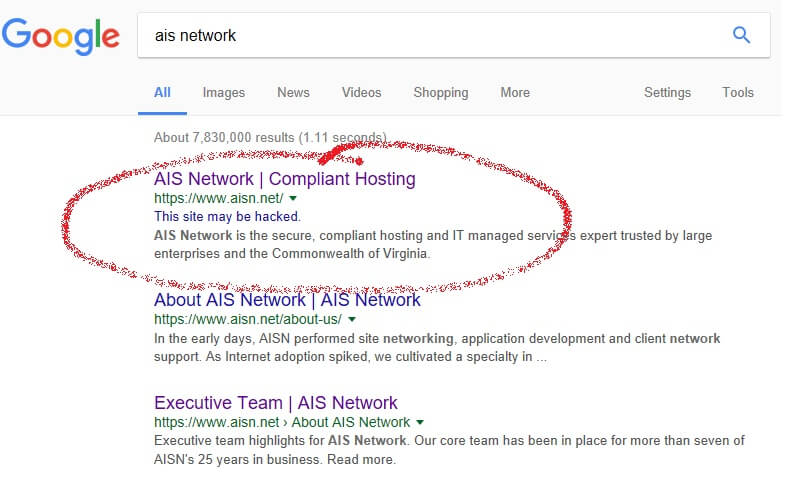
Our Site Was Not Hacked
July 14, 2017
Blog
No. Our site was not hacked. Period. Yesterday, a customer Googled us only to find this — under our name, a notation from Google, which ...
Read More →
Passing Your SOC 2 Audit
June 29, 2017
Compliance
How should you prepare for passing your SOC 2 audit? The pressure is on as more and more service providers and service organizations are being ...
Read More →
WannaCrypt Ransomware Defense
May 16, 2017
Security & Privacy
Looking for WannaCrypt ransomware defense? On Friday, May 12th, a large ransomware attack was launched, known as WannaCrypt (a.k.a. WannaCry). It infected more than 230,000 ...
Read More →
Award-Winning Website Development
May 11, 2017
Design & Development
We’re over the moon this week. Award-winning website development is always what we aim for, and our latest project has done just that. The Virginia ...
Read More →
A Partner You Can Trust
At AISN, we don’t believe that “one size fits all” is the way to offer cloud solutions. Our business model is built on the belief that our clients deserve customized cloud platforms designed to meet their specific compliance, security and operational needs.
If you have questions about the cloud or cloud enablement services, we have answers. Our experts are always happy to discuss your needs, so get in touch with us today.