What is Information Risk Management?
Internet of Things (IoT) technology is being adopted more rapidly than ever. Experts estimate that 31 billion IoT devices will be connected to the internet this year. Information security is increasingly vital with our reliance on automation, remote work, and artificial intelligence. For example, 47% of companies have embedded at least one instance of AI in standard processes. The more complex our systems become, the greater the threat of attack or breach.
Our increasingly digital and automated world means we generate more data and rely more heavily on that data to keep our businesses running. And as our reliance on technology increases, so do the associated risks. Data breaches can wipe out your company financially and quickly destroy your brand’s reputation. Information risk management programs are no longer a “nice to have” — they’re part of doing business.
Information in all its forms must be protected for your business to thrive. It must be kept secure, whole, and available when needed. This means taking a long, hard look at your current and future risks and taking steps to minimize or eliminate their effect on you, your investors, and your clients.
In this post, we’ll look closer at your business’s threats and the consequences of not taking information risk management seriously.
Threats, Vulnerabilities, and Risks
Technological solutions are a crucial component of your information risk management program. However, the best technologies can’t effectively protect your systems if you don’t implement them correctly as part of a comprehensive information security plan. However, you must know what you’re planning for before you can develop a plan.
Information security threats, vulnerabilities, and risks may sound the same. But they’re not.
Understanding the differences is crucial to developing an effective information risk management strategy.

Threats
In information risk management terms, a threat refers to a new incident or event that can somehow harm your organization. There are several different types of threats your business may encounter.
- Natural: Disasters like floods, hurricanes, earthquakes, or tornadoes
- Intentional: Attacks, including worms, viruses, malware, or malicious actions taken by a person or persons
- Unintentional: Accidental incidents, like an employee accessing data they shouldn’t by mistake
Vulnerabilities
Unlike threats, vulnerabilities are not specific to an event or action. Vulnerabilities are weaknesses in your system that can leave your organization open to damage from natural, intentional, and unintentional threats. Your information risk management strategy should include a risk assessment to identify vulnerabilities in your operations so that you can develop an information security program to eliminate them. Common vulnerabilities include:
- Unsecured networks
- Employee credentials that aren’t regularly updated
- Unpatched firewalls or antivirus software
- Irregular or missing backups
Risks
When you combine threats and vulnerabilities, you get risk.
Risks are the potential damages your company may incur when the worst happens, including financial loss, disruption of operations, or a hit to your brand’s reputation. Stories of data breaches caused by any number of threats or vulnerabilities are in the news almost daily.
Varonis says an average of 7 million data records are compromised worldwide daily.
The Ponemon Institute reports:
|
$3.92 million The average data breach costs a company $3.92 million. |
279 days On average, it takes 279 days to identify and contain a breach. |
25,000 records On average, over 25,000 records are compromised in a data breach. |
Information Risk Management
Considering the costs and damages your organization may face due to information security threats and vulnerabilities, it’s not hard to see the value of information risk management. But what does that entail?
Information risk management is preparing for and controlling information technology’s various threats and vulnerabilities. There are two critical components of any information risk management strategy:
- Risk Assessment: Identifying threats and vulnerabilities, estimating their likelihood, and prioritizing risks to develop an effective response.
- Risk Treatment: Actions taken to remediate, mitigate, avoid, prevent, accept, transfer, or manage risks identified in the assessment phase, including establishing governance, training employees, and responding to cybersecurity incidents.
Start Protecting Your Business
As information technology risks increase, more and more businesses and government agencies are prioritizing investments in information risk management. More than half of respondents in an Experian survey said they were enlisting the help of third-party professionals to protect their business-critical data and systems.
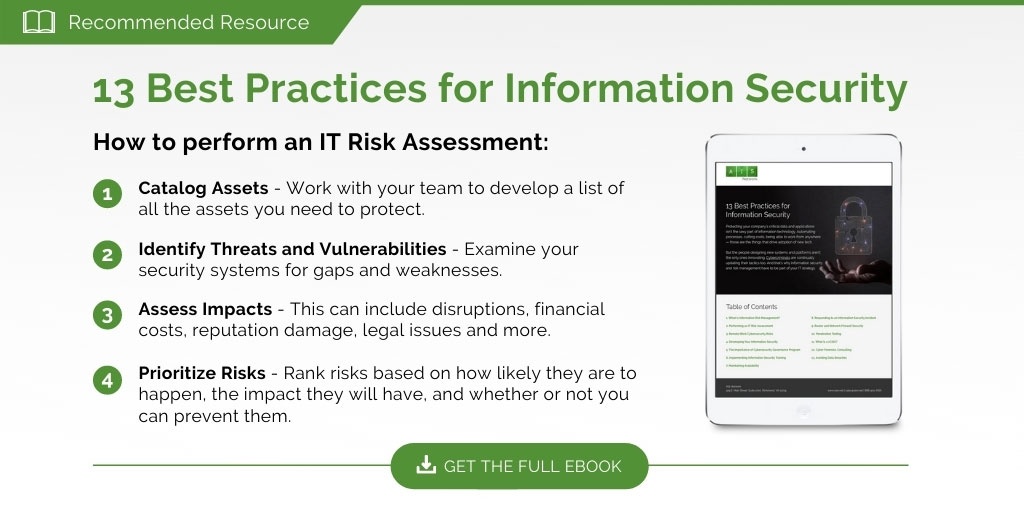
To learn more about managing your IT risks, check out How to Perform an IT Risk Assessment.
At AISN, our strategies are based on The National Institute of Standards and Technology’s Cybersecurity Framework, a voluntary system of standards, guidelines, and practices that promote the protection of critical infrastructure. We offer expert support in developing and implementing a risk management program from risk assessment to penetration testing to employee training. If you’ve got cybersecurity questions, get in touch with us today.