Ensuring Security and Compliance
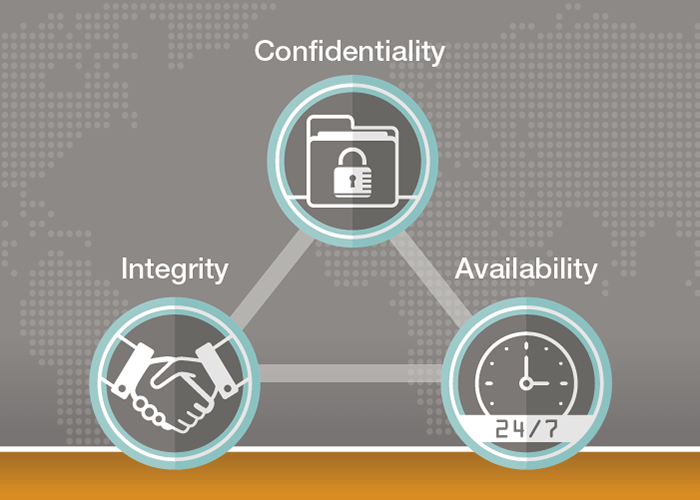
Most organizations tend to focus on becoming compliant rather than being secure. And while meeting client requirements and industry regulations is very important, it does not necessarily guarantee that your organization is secure. If your entire information security program is based on “What must we do to be compliant?”, you’re probably missing some major holes … Read more