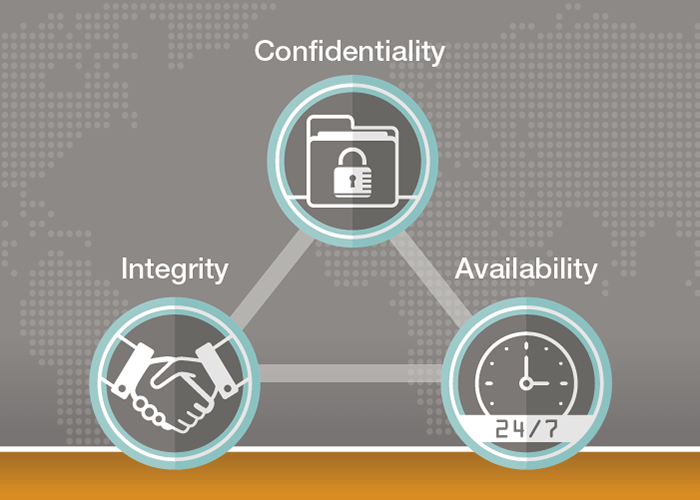
Information Security Program Is Critical
An information security program is a critical component of any organization regardless of the size of your business or the industry you’re in. A good information security program consists of a comprehensive set of information security policies and procedures, which is the cornerstone to any information security program. Whether you’re responsible for protected health information … Read more